用户:Hello World I'm Dad
| 这是维基百科用户页 此页面不是百科全书条目,也不是条目的讨论页。 若您在中文维基百科(域名为zh.wikipedia.org)之外的网站看到此页面,那么您可能正在浏览一个镜像网站。 请注意:镜像网站中的页面可能已经过时,且页面中涉及的用户可能与该镜像网站没有任何关系。 若欲造访原始页面,请点击这里。 |
 | 学业为重,Hello World I'm Dad由于课业因素,正在放一段维基假期,预定会在心情愉快之后回来。 在这期间,Hello World I'm Dad仍可能会时常小幅编辑一下,但给Hello World I'm Dad的留言可能无法很快得到回复。 |
未来
|
记事
|
观点
|
喜好
|
一般
|
语言
|
快速连结
[编辑]下载量农场
广告堆叠
Click Spam
Click Injection
应用程式内事件
规避技术
SDK spoofing
| 由于已知的技术原因,图表暂时不可用。带来不便,我们深表歉意。 |
签名区
[编辑]testHello World I'm Dad(留言) 2019年8月13日 (二) 13:32 (UTC)
朋友你好,很高兴认识你!--向史公哲曰(留言) 2024年8月14日 (三) 16:16 (UTC)
点击欺诈
[编辑]此条目可参照外语维基百科相应条目来扩充。 |
每点击付费模式[编辑] |
Pay-per-click advertising[编辑]Main article: Pay-per-click PPC advertising is an arrangement in which webmasters (operators of websites), acting as publishers, display clickable links from advertisers in exchange for a charge per click. As this industry evolved, a number of advertising networks developed, which acted as middlemen between these two groups (publishers and advertisers). Each time a (believed to be) valid Web user clicks on an ad, the advertiser pays the advertising network, which in turn pays the publisher a share of this money. This revenue-sharing system is seen as an incentive for click fraud. The largest of the advertising networks, Google's AdWords/AdSense and Yahoo! Search Marketing, act in a dual role, since they are also publishers themselves (on their search engines).[2] According to critics, this complex relationship may create a conflict of interest. This is because these companies lose money to undetected click fraud when paying out to the publisher but make more money when collecting fees from the advertiser. Because of the spread between what they collect and pay out, unfettered click fraud would create short-term profits for these companies.[citation needed] |
组织性点击欺诈[编辑]除了平台主个人的点击欺诈案件之外,许多大规模点击欺诈也正在发生。[2]想从事大规模点击欺诈的人通常会使用模拟人类行为的自动程式去点击网页上的广告[3],然而这些点击看起来都像是来自同一个人、少量的电脑或是同一个地区,对于广告主和广告网路来说会十分可疑,若想从事大规模点击欺诈,只有一台电脑的话会很容易被发现。 一种规避透过IP特征侦测点击欺诈的机制的方法是将现有的用户流量转换成点击和曝光(impression)。[4]欺诈者可以透过放置十分微小且一直重新载入的广告以达到对用户伪装的效果,并且和广告主保证所谓的“网页爬虫”浏览的都是正常的网页,而呈给用户点击欺诈用的网页。 细小广告以及其他利用用户的技术还能与透过奖励制造的流量并用,像是“有偿阅读”(Paid to Read)网站的会员在浏览网站或点击关键字的时候能得到少量的钱,[5]而有些有偿阅读网站的管理者也是每点击付费的会员,他们可能会给经常搜寻的人寄特别多的广告邮件,因为关键字的每点击付费常常是网站的唯一收入。这被称为强迫搜寻,是一个在线上有偿购买用户行为的产业中不被赞同的行为。 组织性的点击欺诈可以透过使用非常多的电脑组成犯罪网路从而 使虚假流量的来源显示在许多位置。由于自动程式仍然无法完全模拟用户行为,点击欺诈网路可能会透过感染他人组成僵尸网路或是域名伺服器快取污染等方法使得一般用户在不知情的情况下为他们制造收入。广告主、广告网路以及警察将会十分难以追查散布在各个国家的点击欺诈网路。 曝光数欺诈是被用于拉低对手的广告排序,当竞争对手的广告点击率过低的时候,他们就有可能受到惩罚,广告可能会遭到替换,使得出价较低的广告得以被换上。[6]
|
Organization[编辑]Click fraud can be as simple as one person starting a small Web site, becoming a publisher of ads, and clicking on those ads to generate revenue. Often the number of clicks and their value is so small that the fraud goes undetected. Publishers may claim that small amounts of such clicking is an accident, which is often the case.[citation needed] Much larger-scale fraud also occurs.[3] Those engaged in large-scale fraud will often run scripts which simulate a human clicking on ads in Web pages.[4] However, huge numbers of clicks appearing to come from just one, or a small number of computers, or a single geographic area, look highly suspicious to the advertising network and advertisers. Clicks coming from a computer known to be that of a publisher also look suspicious to those watching for click fraud. A person attempting large-scale fraud, from one computer, stands a good chance of being caught. One type of fraud that circumvents detection based on IP patterns uses existing user traffic, turning this into clicks or impressions.[5] Such an attack can be camouflaged from users by using 0-size iframes to display advertisements that are programmatically retrieved using JavaScript. It could also be camouflaged from advertisers and portals by ensuring that so-called "reverse spiders" are presented with a legitimate page, while human visitors are presented with a page that commits click fraud. The use of 0-size iframes and other techniques involving human visitors may also be combined with the use of incentivized traffic, where members of "Paid to Read" (PTR) sites are paid small amounts of money (often a fraction of a cent) to visit a website and/or click on keywords and search results, sometimes hundreds or thousands of times every day[6] Some owners of PTR sites are members of PPC engines and may send many email ads to users who do search, while sending few ads to those who do not. They do this mainly because the charge per click on search results is often the only source of revenue to the site. This is known as forced searching, a practice that is frowned upon in the Get Paid To industry. Organized crime can handle this by having many computers with their own Internet connections in different geographic locations. Often, scripts fail to mimic true human behavior, so organized crime networks use Trojan code to turn the average person's machines into zombie computers and use sporadic redirects or DNS cache poisoning to turn the oblivious user's actions into actions generating revenue for the scammer. It can be difficult for advertisers, advertising networks, and authorities to pursue cases against networks of people spread around multiple countries. Impression fraud is when falsely generated ad impressions affect an advertiser's account. In the case of click-through rate based auction models, the advertiser may be penalized for having an unacceptably low click-through for a given keyword. This involves making numerous searches for a keyword without clicking of the ad. Such ads are disabled[7] automatically, enabling a competitor's lower-bid ad for the same keyword to continue, while several high bidders (on the first page of the search results) have been eliminated. Hit inflation attack[编辑]A hit inflation attack is a kind of fraudulent method used by some advertisement publishers to earn unjustified revenue on the traffic they drive to the advertisers’ Web sites. It is more sophisticated and harder to detect than a simple inflation attack. This process involves the collaboration of two counterparts, a dishonest publisher, P, and a dishonest Web site, S. Web pages on S contain a script that redirects the customer to P's Web site, and this process is hidden from the customer. So, when user U retrieves a page on S, it would simulate a click or request to a page on P's site. P's site has two kinds of webpages: a manipulated version, and an original version. The manipulated version simulates a click or request to the advertisement, causing P to be credited for the click-through. P selectively determines whether to load the manipulated (and thus fraudulent) script to U's browser by checking if it was from S. This can be done through the Referrer field, which specifies the site from which the link to P was obtained. All requests from S will be loaded with the manipulated script, and thus the automatic and hidden request will be sent.[8] This attack will silently convert every innocent visit to S to a click on the advertisement on P's page. Even worse, P can be in collaboration with several dishonest Web sites, each of which can be in collaboration with several dishonest publishers. If the advertisement commissioner visits the Web site of P, the non-fraudulent page will be displayed, and thus P cannot be accused of being fraudulent. Without a reason for suspecting that such collaboration exists, the advertisement commissioner has to inspect all the Internet sites to detect such attacks, which is infeasible.[8] Another proposed method for detection of this type of fraud is through use of association rules.[9] |
操纵有机搜寻结果[编辑]影响一个网页在有机搜寻中的排名的一个重要因素就是点击率,计算方法是将点击数除以曝光数,或者说将一个搜寻结果被点击的次数除以搜寻结果被展示的次数。 和每点击付费欺诈相反,当你的竞争对手正在购买僵尸网路服务或是低价劳力以产生虚假点击时,点击率欺诈的目的就是将竞争对手的点击率降低,从而不断地降低他们的网站在搜寻引擎最佳化中的排名。 更坏的点击率欺诈者或许还会在削弱对手的同时提升自己网站的排名,或是他的政治立场等。我们对于这个问题上演的规模还不清楚,但很明显有许多网站开发者都很在意网站在分析工具上的指标。 |
Manipulation of organic search results[编辑]One major factor that affects the ranking of websites in organic search results is the CTR (Click-through Rate). That is the ratio of clicks to impressions, or in other words how many times a search result is clicked on, as compared to the number of times the listing appears in search results. In contrast to PPC fraud, where a competitor leverages the services of a botnet, or low cost labour, to generate false clicks, in this case the objective is to beggar thy competitor by making their CTR rate as low as possible, thereby diminishing their ranking factor (position from the top of search results). Bad actors will therefore generate false clicks on organic search results that they wish to promote, while avoiding search results they wish to demote. This technique can effectively create a cartel of business services controlled by the same bad actor, or be used to promote a certain political opinion etc. The scale of this issue is unknown, but is certainly evident to many website developers who pay close attention to the statistics in webmaster tools. |
法律案件[编辑][10][11][12][13][14][15][16][17][18][19][20][21]
|
Legal cases[编辑]Lawsuits[编辑]
Michael Anthony Bradley[编辑]In 2004, California resident Michael Anthony Bradley created Google Clique, a software program that he claimed could let spammers defraud Google out of millions of dollars in fraudulent clicks, which ultimately led to his arrest and indictment.[17] Bradley used technology that he created for his other companies that took him five years to develop. Using this technology, he was able to demonstrate that fraud was possible, and was impossible for Google to detect. Bradley notified Google of this security flaw, and was willing to work with them to close up some of these holes. However, Bradley was offered $500,000 for his software and technology by some of the world's top spammers. With this information, Bradley thought he could put a price of $100,000 on his technology, and offered to sell Google all rights to his technology, and they could make the Internet a better and safer place. When Bradley showed up to Google's offices, he demonstrated the software for them, and when they asked what he wanted, he had stated that he would consult for free if they wanted to purchase the rights to his technology. He explained the prior offer of $500,000 and said he knew he could get it, but would settle for $100,000 if they wanted to work together. Bradley returned to Google's offices and was met by United States Secret Service officers who were undercover. They kept asking him what he wanted, and they even pushed a check for $100,000 to him. Bradley stated that this felt like blackmail and was not comfortable with this, and pushed the money away. Just then the Secret Service came in and arrested him. Authorities said he was arrested while trying to extort $100,000 from Google in exchange for handing over the program.[18] Charges were dropped without explanation on November 22, 2006; both the US Attorney's office and Google declined to comment. Business Week suggests that Google was unwilling to cooperate with the prosecution, as it would be forced to disclose its click fraud detection techniques publicly.[19] Fabio Gasperini[编辑]On June 18, 2016, Fabio Gasperini, an Italian citizen, was extradited to the United States on click fraud charges.[20] An indictment charged Gasperini with:
According to the U.S. government, Gasperini set up and operated a botnet of over 140,000 computers around the world. This was the first click fraud trial in the United States. If convicted of all counts, Gasperini risked up to 70 years in jail. Simone Bertollini, an Italian-American lawyer, represented Gasperini at trial. On August 9, 2017 a jury acquitted Gasperini of all the felony charges of the indictment. Gasperini was convicted of one misdemeanor count of obtaining information without a financial gain. Gasperini was sentenced to the statutory maximum of one year imprisonment, a $100,000 fine, and one year of supervised release following incarceration. Shortly after he was credited with time served and sent back to Italy. An appeal is currently pending.[21] |
应对方案[编辑]
|
Solutions[编辑]Proving click fraud can be very difficult, since it is hard to know who is behind a computer and what their intentions are. When it comes to mobile ad fraud detection, data analysis can give some reliable indications. It is important to understand that abnormal metrics can hint at the presence of different types of frauds. To detect click fraud in ad campaign, advertisers can focus on the following attribution points:
Often the best an advertising network can do is to identify which clicks are most likely fraudulent and not charge the account of the advertiser. Even more sophisticated means of detection are used,[22] but none are foolproof. The Tuzhilin Report[23] produced as part of a click fraud lawsuit settlement, has a detailed and comprehensive discussion of these issues. In particular, it defines "the Fundamental Problem of invalid (fraudulent) clicks":
The PPC industry is lobbying for tighter laws on the issue. Many hope to have laws that will cover those not bound by contracts. A number of companies are developing viable solutions for click fraud identification and are developing intermediary relationships with advertising networks. Such solutions fall into two categories:
In a 2007 interview in Forbes, Google click fraud czar Shuman Ghosemajumder said that one of the key challenges in click fraud detection by third-parties was access to data beyond clicks, notably, ad impression data.[24] Click fraud is less likely in cost per action models. |
研究[编辑]
|
Research[编辑]The fact that the middlemen (search engines) have the upper hand in the operational definition of invalid clicks is the reason for the conflict of interest between advertisers and the middlemen, as described above. This is manifested in the Tuzhilin Report[23] as described above. The Tuzhilin report did not publicly define invalid clicks and did not describe the operational definitions in detail. Rather, it gave a high-level picture of the fraud-detection system and argued that the operational definition of the search engine under investigations is "reasonable". One aim of the report was to preserve the privacy of the fraud-detection system in order to maintain its effectiveness. This prompted some researchers to conduct public research on how the middlemen can fight click fraud.[25] Since such research is presumably not tainted by market forces, there is hope that this research can be adopted to assess how rigorous a middleman is in detecting click fraud in future law cases. The fear that this research can expose the internal fraud-detection system of middlemen still applies. An example of such research is that done by Metwally, Agrawal and El Abbadi at UCSB. Other work by Majumdar, Kulkarni, and Ravishankar at UC Riverside proposes protocols for the identification of fraudulent behavior by brokers and other intermediaries in content-delivery networks. |
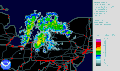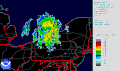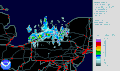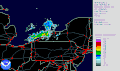
热图
[编辑]
种类[编辑]
|
 Types[编辑]There are different kinds of heat maps:
|
配色[编辑] |
Color schemes[编辑]Many different color schemes can be used to illustrate the heat map, with perceptual advantages and disadvantages for each. Rainbow color maps are often used, as humans can perceive more shades of color than they can of gray, and this would purportedly increase the amount of detail perceivable in the image. However, this is discouraged by many in the scientific community, for the following reasons:[29][30][31][32][33]
|
与等值线图的比较[编辑] |
Choropleth maps vis-à-vis heat maps[编辑]Choropleth maps are sometimes incorrectly referred to as heat maps. A choropleth map features different shading or patterns within geographic boundaries to show the proportion of a variable of interest, whereas the coloration a heat map (in a map context) does not correspond to geographic boundaries.[34] |
实际软体应用[编辑] |
Software implementations[编辑]Several heat map software implementations are freely available:
|
图例[编辑] |
|
- ^ Asdemir, Kursad; Yurtseven, Özden; Yahya, Mon. An Economic Model of Click Fraud in Publisher Networks. 2008.
- ^ Schonfeld, Erick; The Evolution Of Click Fraud: Massive Chinese Operation DormRing1 Uncovered". TechCrunch. October 8, 2009.
- ^ Badhe, Anup. Click Fraud Detection in mobile ads served in programmatic exchanges (PDF). International Journal of Scientific & Technology Research. April 2016, 05: 1.
- ^ Gandhi, Mona; Jakobsson, Markus; Ratkiewicz, Jacob;Badvertisements: Stealthy Click-Fraud with Unwitting Accessories 互联网档案馆的存档,存档日期2016-03-04.", APWG eFraud conference, 2006
- ^ V. Anupam; A. Mayer; K. Nissim; B. Pinkas; M. Reiter. On the Security of Pay-Per-Click and Other Web Advertising Schemes. In Proceedings of the 8th WWW International World Wide Web Conference (PDF). Unizh.co: 1091–1100. 1999.
- ^ A. Metwally; D. Agrawal; A. El Abbadi. Using Association Rules for Fraud Detection in Web Advertising Networks. In Proceedings of the 10th ICDT International Conference on Database Theory (PDF): 398–412. 2005. An extended version appeared in a University of California, Santa Barbara, Department of Computer Science, technical report 2005-23.
- ^ Grow, Bryan; Elgin, Ben; with Herbst, Moira. Click Fraud: The dark side of online advertising. BusinessWeek. October 2, 2006.
- ^ Botnets strangle Google Adwords campaigns, Keyword Hijacking Risk. The Register. [2005-02-04].
- ^ V. Anupam; A. Mayer; K. Nissim; B. Pinkas; M. Reiter. On the Security of Pay-Per-Click and Other Web Advertising Schemes. In Proceedings of the 8th WWW International World Wide Web Conference (PDF). Unizh.co: 1091–1100. 1999.
- ^ Davis, Wendy; "Google Wins $75,000 in Click Fraud Case" 互联网档案馆的存档,存档日期2009-01-22.. Media Post July 5, 2005.
- ^ Ryan, Kevin M. Big Yahoo Click Fraud Settlemen. iMedia Connection. July 5, 2006.
- ^ Wong, Nicole; "Update Lanes Gifts v. Google". Google Blog, March 8, 2006
- ^ Griffin, Joe E. Lanes v. Google Final Order (PDF). Googleblog.blogsport.com. July 27, 2006.
- ^ Sullivan, Danny;"Google Agrees To $90 Million Settlement In Class Action Lawsuit Over Click Fraud" 互联网档案馆的存档,存档日期2007-11-22.. March 8, 2006
- ^ Court Docket For: Lane's Gifts and Collectibles, L.L.C. et al. v. Yahoo! Inc., et al.. Docket Alarm, Inc. [6 August 2013].
- ^ Stricchiola, Jessie. Lost Per Click. Search Engine Watch. July 28, 2004.
- ^ Criminal Docket for: USA v. Bradley, 5:04-cr-20108 (N.D.Cal.). Docket Alarm, Inc. [6 August 2013].
- ^ US Department of Justice; "Computer Programmer Arrested for Extortion and Mail Fraud Scheme Targeting Google, Inc." 互联网档案馆的存档,存档日期2006-10-01.. March 18, 2004
- ^ Elgin, Ben; "The Vanishing Click Fraud Case". Business Week. December 4, 2006
- ^ Cybercriminal Who Created Global Botnet Infected With Malicious Software Extradited To Face Click Fraud Charges. www.justice.gov. [2017-11-21] (英语).
- ^ Cybercriminal Convicted of Computer Hacking and Sentenced to Statutory Maximum. www.justice.gov. [2017-11-21] (英语).
- ^ Ghosemajumder, Shuman; "Using data to help prevent fraud". March 18, 2008
- ^ Tuzhilin, Alexander; The Lane's Gifts v. Google Report, by Alexander Tuzhilin. July, 2006
- ^ Greenberg, Andy; "Counting Clicks". Forbes. September 14, 2007
- ^ Tuzhilin, Alexander; The Lane's Gifts v. Google Report, by Alexander Tuzhilin. July, 2006
- ^ Jansen, B. J. (2007) Click fraud. IEEE Computer. 40(7), 85-86.
- ^ MH370 – Definition of Underwater Search Areas (PDF) (报告). Australian Transport Safety Bureau. 3 December 2015.
- ^ Perrot, A.; Bourqui, R.; Hanusse, N.; Lalanne, F.; Auber, D. Large interactive visualization of density functions on big data infrastructure. 2015: 99–106. ISBN 978-1-4673-8517-6. doi:10.1109/LDAV.2015.7348077 (英语).
|journal=被忽略 (帮助) - ^ 29.0 29.1 29.2 29.3 Borland, David; Taylor, Russell. Rainbow Color Map (Still) Considered Harmful. IEEE Computer Graphics and Applications. 2007, 27 (2): 14–7. PMID 17388198. doi:10.1109/MCG.2007.323435.
- ^ How NOT to Lie with Visualization – Bernice E. Rogowitz and Lloyd A. Treinish – IBM Thomas J. Watson Research Center, Yorktown Heights, NY
- ^ Harrower, Mark; Brewer, Cynthia A. ColorBrewer.org: An Online Tool for Selecting Colour Schemes for Maps. Dodge, Martin; Kitchin, Rob; Perkins, Chris (编). The Cartographic Journal. 2003: 27–37. ISBN 978-0-470-98007-1. doi:10.1179/000870403235002042.
- ^ Green, D. A. A colour scheme for the display of astronomical intensity images. Bulletin of the Astronomical Society of India. 2011, 39: 289–95. Bibcode:2011BASI...39..289G. arXiv:1108.5083
 .
.
- ^ 33.0 33.1 Borkin, M.; Gajos, K.; Peters, A.; Mitsouras, D.; Melchionna, S.; Rybicki, F.; Feldman, C.; Pfister, H. Evaluation of Artery Visualizations for Heart Disease Diagnosis. IEEE Transactions on Visualization and Computer Graphics. 2011, 17 (12): 2479–88. CiteSeerX 10.1.1.309.590
 . PMID 22034369. doi:10.1109/TVCG.2011.192.
. PMID 22034369. doi:10.1109/TVCG.2011.192.
- ^ Choropleth vs. Heat Map –. www.gretchenpeterson.com.
- ^ Using R to draw a heat map from Microarray Data. Molecular Organisation and Assembly in Cells. 26 Nov 2009.
- ^ Draw a Heat Map. R Manual.
- ^ Galili, Tal; O'Callaghan, Alan; Sidi, Jonathan; Sievert, Carson. heatmaply: an R package for creating interactive cluster heat maps for online publishing. Bioinformatics. 2017, ? (?): 1600–1602. PMC 5925766
 . PMID 29069305. doi:10.1093/bioinformatics/btx657.
. PMID 29069305. doi:10.1093/bioinformatics/btx657.
- ^ http://gnuplot.sourceforge.net/demo_4.4/heatmaps.html[需要完整来源]
- ^ Fusion Tables Help - Create a heat map. Jan 2018. support.google.com
- ^ http://www.mrao.cam.ac.uk/~dag/CUBEHELIX/[需要完整来源]
- ^ ol/layer/Heatmap~Heatmap. OpenLayers. [2019-01-01].
- ^ https://www.highcharts.com/demo#heat-and-tree-maps[需要完整来源]
- 因课业因素不活跃的维基人
- 认为条目数量先于品质的维基人
- 中文维基人
- 曾患H1N1新型流感的维基人
- 认为性别无差异的维基人
- 反对版权的维基人
- 赞同知难行易维基人
- 唯我论维基人
- 反对整形的维基人
- 认为睡觉浪费时间的维基人
- 信奉虚无主义的维基人
- 维基无神论者
- 支持哥本哈根解释的维基人
- 信仰或支持多世界理论的维基人
- 支持无政府主义的维基人
- 讨厌善待动物组织的维基人
- 喜欢绿色的维基人
- 维基转笔狂
- 喜欢心理学的维基人
- 热衷于信息学的维基人
- 电子学专题参与者
- 爱好电子学或电子工程的维基人
- 维基程序员
- 喜欢维基百科的维基人
- 喜欢理查德·费曼的维基人
- 未成年的维基人
- 戴眼镜的维基人
- 性别不明的维基人
- 自认是无性恋的维基人
- 独身主义的维基人
- 喜欢下雨天的维基人
- 悲观的维基人
- 经常熬夜的维基人
- 觉得堆砌用户框很吃力的维基人
- 运行Tor节点的维基人
- Telegram使用者
- Firefox 使用者
- Zh 母语使用者
- En-3 使用者
- La-1 使用者
- Bureau-5 使用者
- Python 使用者
- Js 使用者
- C 使用者
- Java 使用者
- Ruby 使用者